Warning: in_array() expects parameter 2 to be array, null given in /home/dmdcweb/public_html/libraries/cms/application/cms.php on line 244
Warning: Creating default object from empty value in /home/dmdcweb/public_html/components/com_k2/views/itemlist/view.html.php on line 539

knowledge sharing (12)
Criteria Websites 2019
Save your Google+ content before March 31, 2019
(Source was taken from: Google+ Team Email <This email address is being protected from spambots. You need JavaScript enabled to view it.>)
You’ve received this email because you have content in Google+ for your personal (consumer) account or a Google+ page you manage.
This is a reminder that on April 2, 2019 we’re shutting down consumer Google+ and will begin deleting content from consumer Google+ accounts. Photos and videos from Google+ in your Album Archive and your Google+ pages will also be deleted.
Downloading your Google+ content may take time, so get started before March 31, 2019.
No other Google products (such as Gmail, Google Photos, Google Drive, YouTube) will be shut down as part of the consumer Google+ shutdown, and the Google Account you use to sign in to these services will remain. Note that photos and videos already backed up in Google Photos will not be deleted.
For more information, see the full Google+ shutdown FAQ.
From all of us on the Google+ team, thank you for making Google+ such a special place.
Google LLC 1600 Amphitheatre Parkway, Mountain View, CA 94043
You have received this mandatory email service announcement to update you about important changes to your Google+ Page, product or account.
What’s the difference between antivirus and anti-malware?
(Source article was taken from: https://www.malwarebytes.com/antivirus/?utm_source=double-opt-in&utm_medium=email-internal-b2c&utm_campaign=EM-B2C-2019-March2-newsletter&utm_content=antivirusmixtape)
Antivirus
Antivirus and anti-malware. Both refer to cybersecurity software, but what do these terms mean, how do they differ, and how do they relate to today’s digital threats?
What’s the difference between antivirus and anti-malware?
For the most part, “antivirus” and “anti-malware” mean the same thing. They both refer to software designed to detect, protect against, and remove malicious software. Contrary to what the name might suggest, antivirus software protects against more than viruses–it just uses a slightly antiquated name to describe what it does. Anti-malware software is designed to protect against viruses too. Anti-malware just uses a more modern name that encompasses all kinds of malicious software, including viruses. That being said, anti-malware can stop a viral infection form happening and remove infected files. However, anti-malware isn’t necessarily equipped to restore files that have been changed or replaced by a virus. Both antivirus and anti-malware fall under the broader term “cybersecurity.”
What is cybersecurity?
Cybersecurity, or computer security, is a catchall term for any strategy for protecting one’s system from malicious attacks aimed at stealing money, personal information, system resources (cryptojacking, botnets), and a whole host of other bad things. The attack might occur on your hardware or software, or through social engineering.
Cybersecurity threats and their countermeasures are varied and nuanced nowadays, but the marketplace naturally strives for simplicity when communicating to consumers. This is why many people still see “viruses” as the biggest threat to their computer. In reality, viruses are just one type of cyberthreat that happened to be popular when computers were in their infancy. They’re far from the most common threat today, but the name stuck. It’s a bit like calling every disease a cold.
“For the most part, antivirus and anti-malware mean the same thing. They both refer to software designed to detect, protect against, and remove malicious software.”
What is a computer virus?
A computer or PC virus is a piece of (usually) harmful software defined by two characteristics:
It needs to be initiated by an unsuspecting user. Triggering a virus can be as simple as opening a malicious email (malspam) attachment or launching an infected program. Once that happens, the virus tries to spread to other systems on the computer’s network or in the user’s list of contacts.
It must be self-replicating. If the software doesn’t self-replicate, it’s not a virus. This process of self-replication can happen by modifying or completely replacing other files on the user’s system. Either way, the resulting file must show the same behavior as the original virus.
Computer viruses have been around for decades. In theory, the origin of “self-reproducing automata” (i.e. viruses) dates back to an article published by mathematician and polymath John von Neumann in the late 1940s. Early viruses occurred on pre-personal computer platforms in the 1970s. However, the history of modern viruses begins with a program called Elk Cloner, which started infecting Apple II systems in 1982. Disseminated via infected floppy disks, the virus itself was harmless, but it spread to all disks attached to a system. It spread so quickly that most cybersecurity experts consider it the first large-scale computer virus outbreak in history.
Early viruses like Elk Cloner were mostly designed as pranks. Their creators were in it for notoriety and bragging rights. However, by the early 1990s, adolescent mischief had evolved into harmful intent. PC users experienced an onslaught of viruses designed to destroy data, slow down system resources, and log keystrokes (also known as a keylogger). The need for countermeasures led to the development of the first antivirus software programs.
Early antivirus programs were exclusively reactive. They could only detect infections after they took place. Moreover, the first antivirus programs identified viruses by the relatively primitive technique of looking for their signature characteristics. For example, they might know there’s a virus with a file name like “PCdestroy,” so if the antivirus program recognized that name, it would stop the threat. However, if the attacker changed the file name, the antivirus might not be as effective. While early antivirus software could also recognize specific digital fingerprints or patterns, such as code sequences in network traffic or known harmful instruction sequences, they were always playing catch up.
Early antiviruses using signature-based strategies could easily detect known viruses, but they were unable to detect new attacks. Instead, a new virus had to be isolated and analyzed to determine its signature, and subsequently added to the list of known viruses. The antivirus user had to regularly download an ever-growing database file consisting of hundreds of thousands of signatures. Even so, new viruses that got out ahead of database updates left a significant percentage of devices unprotected. The result was a constant race to keep up with the evolving landscape of threats as new viruses were created and released into the wild.
Current status of computer viruses and antivirus programs
PC viruses today are more of a legacy threat than an ongoing risk to computer users. They’ve been around for decades and have not substantially changed. In fact, the last truly “new” virus that replicated itself through user interaction occurred in 2011 or 2012.
So if computer viruses aren’t really a thing anymore, why do people still call their threat protection software an antivirus program?
It boils down to entrenched name recognition. Viruses made sensational headlines in the 90s, and security companies began using it as shorthand for cyberthreats in general. Thus, the term “antivirus” was born. Decades later, many security firms still use the term “antivirus” to market their products. It’s become a vicious cycle. Consumers assume viruses are synonymous with cyberthreats, so companies call their cybersecurity products “antivirus” software, which leads consumers to think viruses are still the problem.
But here’s the thing. While “virus” and “antivirus” are not exactly anachronisms, modern cyberthreats are often much worse than their viral predecessors. They hide deeper in our computer systems and are more adept at evading detection. The quaint viruses of yesterday have given rise to an entire rogue’s gallery of advanced threats like spyware, rootkits, Trojans, exploits, and ransomware, to name a few.
As these new attack categories emerged and evolved beyond early viruses, antivirus companies continued their mission against these new threats. However, antivirus companies were unsure how to categorize themselves. Should they continue to market their products as an “antivirus” at the risk of sounding reductive? Should they use another “anti-threat” term to market themselves under like “anti-spyware,” for example? Or was it a better to take an all-inclusive approach, and combine everything in a single product line that addressed all threats? The answers to these questions depends on the antivirus company.
At Malwarebytes, cybersecurity is our highest-level catchall category. And that’s why it makes sense to combine our anti-threat effort into a single term that covers more than just viruses. Accordingly, the term we use to cover most of what we do is “anti-malware,” which is short for “anti-malicious software.”
“Consumers assume viruses are synonymous with cyberthreats, so companies call their cybersecurity products “antivirus” software, which leads consumers to think viruses are still the problem.”
If viruses aren’t as big of a threat anymore, why do I need cybersecurity?
Viruses are just one kind of malware. Though viruses still exist, there are other forms of malware that are more common these days. For example, here are several common threats that Malwarebytes can stop:
Adware is unwanted software designed to throw advertisements up on your screen, most often within a web browser, but sometimes within mobile apps as well. Typically, it either disguises itself as legitimate, or piggybacks on another program to trick you into installing it on your PC, tablet, or mobile device.
Spyware is malware that secretly observes the computer user’s activities without permission, then reports it to the software’s author.
A virus is malware that attaches to another program and, when triggered, replicates itself by modifying other computer programs and infecting them with its own bits of code.
Worms are a type of malware similar to viruses in that they spread, but they don’t require user interaction in order to trigger.
A Trojan, or Trojan horse, is more of a delivery method for infections rather than an infection itself. The Trojan represents itself as something useful in order to trick users into opening it. Trojan attacks can carry just about any form of malware, including viruses, spyware, and ransomware.
Ransomware is a form of malware that locks you out of your device and/or encrypts your files, then forces you to pay a ransom to get them back. Ransomware has been called the cybercriminal’s weapon of choice, because it demands a profitable quick payment in hard-to-trace cryptocurrency. The code for a ransomware attack is easy to obtain through online criminal marketplaces, and defending against it is difficult.
A rootkit is malware that provides the attacker with administrator privileges on the infected system and actively hides from the normal computer user. Rootkits also hide from other software on the system—even from the operating system itself.
A keylogger is malware that records all the user’s keystrokes on the keyboard, typically storing the gathered information, and sending it to the attacker, who is seeking sensitive information like usernames and passwords, or credit card details.
Malicious cryptomining, also sometimes called drive-by mining or cryptojacking, is an increasingly prevalent form of malware or browser-based attack that is delivered through multiple attack methods, including malspam, drive-by downloads, and rogue apps and extensions. It allows someone else to use your computer’s CPU or GPU to mine cryptocurrency like Bitcoin or Monero. So instead of letting you cash in on your computer’s horsepower, the cryptominers send the collected coins into their own account—not yours. So, essentially, a malicious cryptominer is stealing your device’s resources to make money.
Exploits are a type of threat that takes advantage of bugs and vulnerabilities in a system in order to allow the exploit’s creator to deliver malware. Among other threats, exploits are linked to malvertising, an attack that uses malicious ads on mostly legitimate websites to deliver exploits. You needn’t even click on the ad to be affected—exploits and their accompanying malware can install themselves on your computer in a drive-by download. All you have to do is visit a good site on the wrong day.
How does anti-malware work?
The old school method of signature-based threat detection is effective to a degree, but modern anti-malware also detects threats using newer methods that look for malicious behavior. To put it another way, signature-based detection is a bit like looking for a criminal’s fingerprints. It’s a great way to identify a threat, but only if you know what their fingerprints look like. Modern anti-malware takes detection a step further so it can identify threats it has never seen before. By analyzing a program’s structure and behavior, it can detect suspicious activity. Keeping with the analogy, it’s a bit like noticing that one person always hangs out in the same places as known criminals, and has a lock pick in his pocket.
This newer, more effective cybersecurity technology is called heuristic analysis. “Heuristics” is a term researchers coined for a strategy that detects threats by analyzing the program’s structure, its behavior, and other attributes.
Each time a heuristic anti-malware program scans an executable file, it scrutinizes the program’s overall structure, programming logic, and data. All the while, it looks for things like unusual instructions or junk code. In this way, it assesses the likelihood that the program contains malware.
What’s more, a big plus for heuristics is its ability to detect malware in files and boot records before the malware has a chance to run and infect your computer. In other words, heuristics-enabled anti-malware is proactive, not reactive. Some anti-malware products can also run the suspected malware in a sandbox, which is a controlled environment in which the security software can determine whether a program is safe to deploy or not. Running malware in a sandbox lets the anti-malware look at what the software does, the actions it performs, and whether it tries to hide itself or compromise your computer.
Another way heuristic analytics helps keep users safe is by analyzing web page characteristics in order to identify risky sites that might contain exploits. If it recognizes something fishy, it blocks the site.
In brief, signature-based antivirus is like a bouncer at the nightclub door, carrying a thick book of mug shots and booting anyone that matches. Heuristic analysis is the bouncer who looks for suspicious behavior, pats people down, and sends home the ones carrying a weapon.
(Source article was taken from: https://www.eduroam.org/what-is-eduroam/)

What is eduroam?
eduroam (education roaming) is the secure, world-wide roaming access service developed for the international research and education community. Having started in Europe, eduroam has gained momentum throughout the research and education community and is now available in 89 territories. eduroam allows students, researchers and staff from participating institutions to obtain Internet connectivity across campus and when visiting other participating institutions by simply opening their laptop.
Where can I eduroam?
eduroam is available in thousands of locations across over 89 countries worldwide. From campuses to coffee shops. Click here for an interactive map of countries where you can eduroam.
Is it safe?
eduroam is based on the most secure encryption and authentication standards in existence today. Its security by far exceeds typical commercial hotspots. Find out about eduroam security here.
How does eduroam work?
eduroam allows any user from an eduroam participating site to get network access at any institution connected to eduroam. Depending on local policies at the visited institutions, eduroam participants may also have additional resources at their disposal. The user credentials are kept secure because eduroam does not share them with the site you’re visiting. Instead they are forwarded to the user’s home institution, where they can be verified and validated.
The system uses a network of servers run by the institutions, and the participating National Research and Education Networks (NRENs) to securely route these requests back to your home institute. All this happens seamlessly and virtually instantly – all thanks to eduroam!
Does eduroam monitor or filter access?
eduroam provides authenticated network access at any location where the service is enabled. Each participating organisation offering network access to authenticated users is able to apply its own filtering policies as long as it is clearly informing users about the filtering rules.
For more info regarding eduroam, please visit the links provided below:
(International) https://www.eduroam.org/
(Local) https://mon.eduroam.my/
How do I make my website appear on Google?
Written by Mohd Afif Md Jamel KhirHow do I make my website appear on Google?
After you have chosen the final website address and added your content, your website is ready for being included into Google and other search engines.
Websites are not added to Google or other search engines by somebody. They are found and added to search index by search engines themselves. Here is how it works: time after time search engines re-visit the pages they already know about and they look for links to new and undiscovered websites. Once a new website is detected, it is processed and added to the search index.
For your website to be found and indexed by search engines, you must do one of the following:
- Submit your website to search engines
- Arrange that a link to your website is included in a website that already shows up in search
Submit your website to search engines
Once your website is created, you must tell search engines that it exists. The fastest way to do this is by submitting your website directly to the major search engines.
After you have submitted your website to search engines, it may take anywhere from a week to a month for search engines to crawl and index your website. This is normal and should be expected. Also, once your website is indexed, there is no guarantee that Google, or other search engines, will decide to rank you very highly within the search results. But do not worry, there are many things you can do to improve your results.
Arrange that a link to your website is included in a website that already shows up in search
If a link to your website is present on another website that is already indexed by the search engine, then after some days or weeks your website will be picked up and indexed as well. Here are some places where you may publish your link:
- Well established websites of your friends or partners
- Your other websites that are already included in the search index
- Your social media profiles
- Forums and discussion boards
Related topics
How Do I Get My Site On Google?
First, you need to make sure your website has been indexed by Google. To find out if it is, type site:yourdomain.com into the Google search box, replacing yourdomain.com with your actual domain name. If you see a listing of your website's pages, then Google has already indexed your site and will continue to visit it occasionally to check for updates. If your website is not listed, submit it here: https://www.google.com/addurl. It will take 1 or 2 weeks for Google to visit and index your website.
Secondly, remember, Google will only display web pages that are relevant to the keyword being searched. The first step is to make sure your web page's text is related to the keyword in question. If it's not, chances are Google won't show it.
Third, just because your website does not show up on the first page, doesn't mean it is not showing up at all. Go to the bottom of the results page and click "Next" for page 2 and so on. Your website may be on page 2, page 82 or somewhere in between.
Okay, My Website Is On Google, But It's On Page 41! How Do I Get It To Show On Page 1?
Ah! You've asked the million dollar question. An entire industry has been built to answer this question and millions of dollars are spent each year to accomplish this! My first question for you is, "How much money do you have?" Just kidding, but seriously, the good news is there are two main ways to get your website to show up on the first page of Google:
- You can pay to be on the first page of Google and it doesn't have to be a lot of money. This is called Google Ads.
- You can get your website to rank "organically" without having to pay for ads.
I'll explain both below...
Google Ads (Pay to Play!)
The quickest and easiest way to get on page 1 of Google for a particular keyword is to pay for an advertisement. You sign up with Google, choose the keywords you would like to target, then "bid" (yes, like an auction) on how much you would like to pay every time your ad is clicked on. This is called "pay-per-click". The higher you bid per click, the higher your ad will appear to the top of the page, all other things being equal.
You can also set a daily budget so that when your budget is met, Google will not show your ad any more that day so it won't be clicked on and you won't be charged. For most industries, this is a cheap and easy way to show up on Google's first page.
For other industries (like lawyers, for example), it can be very expensive. Some keywords cost up to $100 per click or more!
Consider Hiring a Google Ads Pro
Be careful with Google Ads. They make it very easy to sign up and start showing ads on their platform (Bing has a very similar platform). But if you don't know what you are doing, you can waste a lot of money with Google Ads. Considering the fact that I happen to be a professional who is certified by Google in AdWords campaign creation, management and optimization, I suggest you leave it up to a pro to create and manage your Google Ads campaigns.
If the professional or agency you hire knows what they are doing, they will more than pay for themselves when it comes to return on investment. For example, if your pro or agency charges you a fee of $1,500/mo to manage and optimize your AdWords campaigns, and they are doing things right, you should get much more than a $1,500/mo benefit from having hired them.
There are literally hundreds of different settings and features you can add or tweak for any one Google Ads campaign. If you don't get them all correct, you could waste or lose out on a lot of money each month. Hire a pro with proven results if you have the budget. If you don't have the budget to hire a pro to manage your Google Ads campaigns, I recommend staying away from paid search advertising.
Psst! Don't forget to get your FREE SEO Audit below.
Getting on Google Organically
The other way to get on page 1 of Google and other search engines is the organic, or natural, method. These are the main results that show up below the ads or local map section on search engine results pages (see graphic above).
These results cannot be achieved by paying money to Google - they are achieved with careful and long-term optimization of many factors that Google uses when ranking relevancy. The practice of optimizing your web presence so that it shows up organically on Google is called Search Engine Optimization (SEO).
Some of the most important factors that influence your Google page 1 ranking are:
- Quality and Length of Your Page Content - Your website's pages should be full of unique and useful information that will benefit your ideal customer or client. The longer the better, as long as it is high quality. Strive to help your target audience by creating quality content that they will want to consume (like this article!).
- Quality and Number of Inbound Links - If other sites are linking to yours, especially big important sites that have content relating to yours, then Google will rank your site higher. Third party links to your website provide a "thumbs up" or vote of confidence that signals to Google that your content might be worth pushing higher up the SERP.
- Mobile Friendly Website - The majority of people are now using mobile phones to search for information on the web. Are your website pages mobile-friendly? Your site should be optimized for mobile devices and easy to navigate so users on any device can find what they need quickly and easily.
- Page Speed - Your web pages should load fast on all devices. Slow loading web pages could negatively affect your ranking on Google. Nobody likes to wait several seconds for any website to load. You can conduct a free page speed test here or use a tool like Gtmetrix to test your website page speed.
- Keywords in Page Content - Obviously, if the keywords you are targeting actually appear on your site in the text and titles of the pages, you will rank better for those keywords. Don't "keyword stuff". That practice is outdated and will only hurt you now. Write your content for humans, but do keep Google in mind. Don't use too many keywords. When in doubt, keep it natural sounding.
- Authority of Domain Name - The longer you've owned the domain, the better. The more pages of quality content you have on your domain name, the better. Also, include keywords in your domain name if you can (although Google says this does not directly impact your rankings, it could help influence a user to click on your website vs a competitor's).
- Secure Pages - Your web pages should load via https so they are secure. Google, and regular humans, like to see secure pages, even if you're not processing credit cards or obtaining personal information. In their Chrome browser, Google is now labeling all pages that load with an SSL as Not Secure. Don't be one of these naughty sites...get an SSL isntalled by your web hosting company so that all your pages load securely.
- URL Structure - "Pretty" URL's are better (https://cristersmedia.com/blog is better than https://cristersmedia.com/index.php&id=54). If your page URL's are human readable, that's a good thing.
Other Things You Should Do to Rank on Google Page 1
Google My Business
Claim and optimize your Google My Business listing, especially if you are a business that serves only your local community (like a bakery or plumber). Then, get as many positive reviews as you can. This will greatly increase your chances of showing up in the Local Map pack section above the first organic listing. This can be huge if you do it correctly!
Start a Blog
One of the single best things you can do to rank highly on Google is to start a blog and post articles regularly. If you're not sure what to write about, think about the top 5 questions your customers ask you. Then write a thorough answer to each question - one blog post per question. Notice the title of this blog post?
Get a Few Quality Links
Partner with a non-profit in your local community and do a contest or giveaway. Maybe the local paper will pick up on it and give you some free PR (and a link to your website). Join your local Chamber of Commerce or BNI and get a listing on their website. Offer to write a guest article for the local paper or neighborhood magazine. They will often include a link to your website in your bio at the end of the article.
Create Citations
What is a citation you ask? A citation is a listing of your business on a local directory site. Go to sites like Yelp, Foursquare, YP.com, Angie's List, etc and make sure your business listing shows up there and that the information is accurate. This helps create a robust link profile for your domain name and will send signals to Google that the information they find on your site can be trusted because it is found on other sites around the web.
You're Never Done
Additionally, just because you rank well for one keyword or key phrase, does not mean you will rank well for a similar key word/phrase. And remember that Google is constantly updating their ranking algorithms so today's rankings may not equal tomorrow's rankings.
Expect to see your site move up and down in the rankings on a daily or weekly basis - it may even drop from the rankings altogether. This is why SEO should always be ongoing.
Remember, your competitors are likely following the same protocols you are. They are likely optimizing their web presence using the same methods you are using. Keep blogging and getting links. Improve the content you already have on your website. A lot of diligence and patience will prove to be worth it when you get that coveted spot at the top of Google page 1. Depending on your business, it could literally be worth millions of dollars in revenue. Something that valuable will never come easy.
source: https://cristersmedia.com/how-do-i-get-my-website-on-the-first-page-of-google/
How to Clean a Hacked Joomla! Site
Written by Sharifah Noor Sahila Syed Jamal(Source article was taken from: https://sucuri.net/guides/how-to-clean-hacked-joomla)
Common Indicators of a Hacked Joomla! Site:
- Blacklist warnings by Google, Bing, McAfee, etc.
- Unexpected or abnormal browser behaviors
- Spam keywords in search engine content
- Host suspended your site for malicious activity
- File modifications or Joomla! core integrity issues
- Malicious new users in the Joomla! dashboard
Step 1: Identify Hack
1.1 Scan Your Site
You can use tools that scan your site remotely to find malicious payloads and malware locations.
To scan Joomla! for hacks:
Visit the SiteCheck website.
- Click Scan Website.
- If the site is infected, review the warning message.
- Note any payloads and locations (if available).
- Note any blacklist warnings.
Tools to scan your website:
- SiteCheck
- UnmaskParasites
- Redleg Aw-Snap
- VirusTotal
1.2 - Check Modified Files
New or recently modified files may be part of the hack. Your core Joomla! files should also be checked for malware injections.
The quickest way to confirm the integrity of your Joomla! core files are by using the diff command in terminal. If you are not comfortable using the command line, you can manually check your files via SFTP.
You can find all Joomla! versions on GitHub. Using an SSH terminal, you can download Joomla! locally. The following commands use version 3.6.4 as an example of the clean files and public_html as an example of where your Joomla! installation is located.
To check core file integrity with SSH commands:
$ mkdir joomla-3.6.4
$ cd joomla-3.6.4
$ wget https://github.com/joomla/joomla-cms/releases/download/3.6.4/Joomla_3.6.4-Stable-Full_Package.tar.gz
$ tar -zxvf Joomla_3.6.4-Stable-Full_Package.tar.gz
$ diff -r joomla-3.6.4 ./public_html
The final diff command will compare the clean Joomla! files with your installation.
To manually check recently modified files:
Log into your server using an FTP client or SSH terminal.
If using SSH, you can list all files modified in the last 15 days using this command:
$ find ./ -type f -mtime -15
If using SFTP, review last modified date column for all files on the server.
Note any files that have been recently modified.
**Note
We recommend using FTPS/SFTP/SSH rather than unencrypted FTP.>
1.3 Audit User Logs
Verify your Joomla! user accounts, especially administrators and super-administrators.
- To check for malicious users in Joomla!:
- Log into your Joomla! Administrator area.
- Click Users on the menu item and select Manage.
- Review the list, especially ones with a recent Registration Date.
- Remove any unfamiliar users that were created by hackers.
- Check the Last Visit Date of legitimate users.
- Confirm any users that logged in at suspicious times.
- You can also parse your server logs if you know where they are stored and how to search for requests to the administrator area of Joomla!
- Users logging in at unusual times or geographic locations may have been compromised.
1.4 - Check Diagnostic Pages
If your Joomla! site has been blacklisted by Google or other website security authorities, you can use their diagnostic tools to check the security status of your Joomla! website.
To check your Google Transparency Report:
- Visit the Safe Browsing Site Status website.
- Enter your site URL and search.
- On this page you can check:
- Site Safety Details: information about malicious redirects, spam, and downloads.
- Testing Details: most recent Google scan that found malware.
If you have added your site to any free webmaster tools, you can check their security ratings and reports for your website. If you do not already have accounts for these free monitoring tools, we highly recommend that you sign up as they are free to use:
- Google Webmasters Central
- Bing Webmaster Tools
- Yandex Webmaster
- Norton SafeWeb
Step 2: Fix Hack
Now that you have information about potentially compromised users and malware locations, you can remove malware from Joomla! and restore your website to a clean state.
Pro Tip:
The best way to identify hacked files is by comparing the current state of the site with an old and clean backup. If a backup is available, you can use that to compare the two versions and identify what has been modified.
2.1 - Clean Hacked Website Files
If any scans or diagnostic pages revealed malicious domains or payloads, you can start by looking for those files on your Joomla! web server. By comparing infected files with known good files (from official sources or reliably clean backups) you can identify and remove malicious changes.
To manually remove a malware infection from your Joomla! files:
- Log into your server via SFTP or SSH.
- Create a backup of the site files before making changes.
- Search your files for reference to malicious domains or payloads you noted.
- Identify recently changed files and confirm whether they are legitimate.
- Review files flagged by the diff command during the core file integrity check.
- Restore or compare suspicious files with clean backups or official sources.
- Remove any suspicious or unfamiliar code from your custom files.
- Test to verify the site is still operational after changes.
If you can't find the malicious content, try searching the web for malicious content, payloads, and domain names that you found in the first step. Chances are that someone else has already figured out how those domain names are involved in the hack you are attempting to clean.
- Diff tools to compare suspicious files with known-good copies:
- DiffNow
- Diff (bash command)
- DiffChecker
- Caution
It is important that you compare the same version of your Joomla! core files and extensions. Core files on the 2.x branch are not the same as the 3.x branch and so on. Never perform any actions without a backup. If you’re unsure, please seek assistance
2.2 Clean Hacked Database Tables
To remove a malware infection from your Joomla! database, you need to open a database admin panel, such as PHPMyAdmin. You can also use tools like Search-Replace-DB or Adminer.
To manually remove a malware infection from Joomla! database tables:
- Log into your database admin panel.
- Make a backup of the database before making changes.
- Search for suspicious content (i.e., spammy keywords, links).
- Open the table that contains suspicious content.
- Manually remove any suspicious content.
- Test to verify the site is still operational after changes.
- Remove any database access tools you may have uploaded.
You can manually search your Joomla! database for common malicious PHP functions, such as eval, base64_decode, gzinflate, preg_replace, str_replace, etc. Note that these functions are also used by Joomla! extensions for legitimate reasons, so be sure you test changes or get help so you do not accidentally break your site.
2.3 - Secure User Accounts
Hackers always leave a way to get back into your site. More often than not, we find multiple backdoors of various types in hacked Joomla! sites. Backdoors are usually embedded in files that are named just like legitimate files within the official Joomla! framework but located in the wrong directories. Attackers can also inject backdoors into files like index.php and directories like /components, /modules, and /templates.
Backdoors commonly include the following PHP functions:
base64
str_rot13
gzuncompress
gzinflate
eval
exec
create_function
location.href
curl_exec
stream
system
assert
stripslashes
preg_replace (with /e/)
move_uploaded_file
strrev
file_get_contents
encodeuri
wget
Caution
These functions can also be used legitimately by Joomla! extensions, so be sure to test any changes because you could break your site by removing benign functions. Always remember to compare files using the same Joomla! version.
To remove backdoors by comparing files:
- Confirm your Joomla! version by clicking the System menu and opening System Information
- Download the same version of known good core files from the version official Joomla! repository.
- Log into your server via SFTP or SSH.
- Create a backup of the site files before making changes.
- In your FTP client, compare your site with the known good download.
- Investigate any new files on your server that do not match the known good files.
- Investigate any files that are not the same size as the known good files.
The majority of malicious code we see uses some form of encoding to prevent detection. Aside from premium components that use encoding to protect their authentication mechanism, it's very rare to see encoding in the official Joomla! repository. It is critical that all backdoors are closed to successfully clean a Joomla! hack, otherwise, your site will be reinfected quickly.
2.4 - Fix Malware Warnings
If you were blacklisted by Google, McAfee, Yandex (or any other webspam authorities), you can request a review after the hack has been fixed. Google is now limiting repeat offenders to one review request every 30 days. Be sure your site is clean before requesting a review!
- To remove malware warnings on your site:
- Call your hosting company and ask them to remove the suspension.
- You may need to provide details about how you removed the malware.
- Fill in a review request form for each blacklisting authority.
- ie. Google Search Console, McAfee SiteAdvisor, Yandex Webmaster.
- The review process can take several days.
Step 3: Post-Hack
In this final step, you will learn how to fix the issues that caused Joomla! to be hacked in the first place. You will also perform essential steps to enhance the security of your Joomla! site.
3.1 - Update and Reset
Outdated software is one of the leading causes of infection, and it is important to remove any known vulnerable extensions. Passwords should also be reset to ensure you are not reinfected if hackers gained access to your credentials.
Update Joomla! Core and Extensions
Update all Joomla! software including core files, components, templates, modules, and plugins. You should also check your extensions for known vulnerabilities using the Joomla! Vulnerable Extensions List.
To check and update Joomla! extensions:
- Make sure you have a recent backup of your site.
- Log into your Joomla! Administrator area.
- Click Extensions on the menu item and select Manage.
- On the sidebar click Update.
- Review available updates and apply them.
- Remove any extensions that contain known vulnerabilities.
Joomla! 3.x is the most stable major versions as they are still actively developed. Users on 1.x and 2.x branches should strongly consider migrating to 3.x and keep the core files updated. If you are manually updating core files, you can safely delete directories that are part of the official Joomla! framework (administrator, components, etc), then manually rebuild those same core directories and components.
To check and update Joomla! core files:
- Make sure you have a recent backup of your site.
- Log into your Joomla! Administrator area.
- Click System on the menu item and select Joomla! Update.
- Click the Check for Updates button.
- Review available updates for your Joomla! version.
- Click the Reinstall Joomla core files button.
- Users on the 1.x branch are strongly encouraged to upgrade to 3.x by following the Joomla! Docs migration guide.
If in the first step SiteCheck identified other outdated software on your server (i.e., Apache, cPanel, PHP), you should update those to ensure you have any available security patches.
Reset User Credentials
You should reset all user passwords with unique, strong passwords to avoid reinfection.
To reset passwords for Joomla! user accounts:
- Log into your Joomla! website.
- Click the Users menu item.
- Open each user account.
- Change the user’s password.
- Repeat for each user on your site.
You should reduce the number of administrator and super-administrator accounts for Joomla!, and all of your website systems. Practice the concept of least privileged. Only give people the access they require to do the job they need. Joomla! comes with built-in two-factor authentication on user accounts.
To enable 2FA on your Joomla! user accounts:
- Log into your Joomla! website.
- Click the Users menu item.
- Open your user account.
- Click the Two Factor Authentication tab.
- Follow the steps to enable 2FA.
- Have each user repeat this process.
It is advisable to reinstall all extensions after a hack to ensure they are functional and free of residual malware. If you have deactivated themes, components, modules, or plugins, we recommend you remove them from your web server.
3.2 - Set Backups
Backups function as a safety net. Now that your Joomla! site is clean and you’ve taken some important post-hack steps, make a backup! Having a good backup strategy is at the core of a good security posture. Here are some tips to help you with website backups:
- Location
Store Joomla! backups in an off-site location. Never store backups (or old versions) on your server; they can be hacked and used to compromise your real site.
- Automatic
Ideally, your backup solution should run automatically at a frequency that suits the needs of your website.
- Redundancy
EV certificates require even more documentation for the Certificate Authority to validate the organization. Visitors will see the name of the business inside the address bar (in addition to clicking the lock icon).
- Testing
Try the restore process to confirm your website functions correctly.
- File Types
Some backup solutions exclude certain file types such as videos and archives.
3.3 - Scan Your Computer
Have all Joomla! users run a scan with a reputable antivirus program on their operating systems. Joomla! can be compromised if a user with an infected computer has access to the dashboard. Some infections are designed to jump from a computer into text editors or FTP clients.
Here are some antivirus programs we recommend:
- Paid
BitDefender, Kaspersky, Sophos, F-Secure.
- Free
Malwarebytes, Avast, Microsoft Security Essentials, Avira.
3.4 - Protect Your Site: Website Firewall
You can harden your Joomla! site by restricting file permissions and implementing custom .htaccess rules. We recommend reviewing the Joomla! Security Docs for more information. The number of vulnerabilities exploited by attackers grows every day. Trying to keep up is challenging for administrators. Website Firewalls were invented to provide a perimeter defense system surrounding your website.
Benefits of using a website firewall:
1. Prevent a Future Hack
By detecting and stopping known hacking methods and behaviors, a website firewall keeps your site protected against infection in the first place.
2. Virtual Security Update
Hackers quickly exploit vulnerabilities in plugins and themes, and unknown ones are always emerging (called zero-days). A good website firewall will patch your holes in your website software even if you haven’t applied security updates.
3. Block Brute Force Attack
A website firewall should stop anyone from accessing your wp-admin or wp-login page if they aren't supposed to be there, making sure they can’t use brute force automation to guess your password.
4. Mitigate DDoS Attack
Distributed Denial of Service attacks attempt to overload your server or application resources. By detecting and blocking all types of DDoS attacks, a website firewall makes sure your site is available if you are being attacked with a high volume of fake visits.
5. Performance Optimization
Most WAFs will offer caching for faster global page speed. This keeps your visitors happy and is proven to lower bounce rates while improving website engagement, conversions, and search engine rankings.
What is Virtual Hardening?
Written by Sharifah Noor Sahila Syed Jamal(Source article was taken from: https://blog.sucuri.net/2018/03/what-is-virtual-hardening.html)
If you want to make your website security more robust, you need to think about hardening. To harden your website means to add different layers of protection to reduce the potential attack surface. Hardening often involves manual measures of adding code or making changes to the configuration. To virtually harden your site involves allowing a Web Application Firewall (WAF) or security plugin to automatically harden your website.
The concept of hardening is part of a defense-in-depth strategy that protects your web server and database from vulnerability exploitation. Similar to other Information Security areas, it is necessary to understand website security in a comprehensive way.
When you add layers of protection to your website, you implement controls that account for:
- The depth of the defense: adding multiple controls to protect your website.
- The breadth of the attack surface: covering all potential attack vectors and security domains.
Adding virtual hardening to a website means protecting it on many levels, such as:
- The application
- The operating system
- The web server
- The database
Website CMS
It is important to emphasize that when it comes to hardening, each environment is unique. For example, if your website is using the WordPress platform, we can give you some tips to harden it, such as:
- Restrict wp-admin access for only certain whitelisted IP addresses
- Disable PHP execution inside the uploads directory
- Disable direct PHP execution inside the whole wp-content directory whenever possible
However, not all WordPress website owners are able to apply these tips for many reasons, such as, not being able to have a whitelist of IPs because your IP is dynamic and so on. It does not mean that you cannot use other methods. In our firewall dashboard, for example, you can add an extra layer of protection by adding an authentication method of your choice. Read our Knowledge Base article to know how it works. Providing hardening tips to all website owners regardless of their CMS can be very difficult.
Web Servers
As we mentioned before, virtual hardening goes beyond the platform environment into your web server, including:
- Windows IIS
- Apache
- NGINX
- Node.js
- Lighttpd
Adding security defenses to your server can be very challenging. You will need to know which server you are running on and to research server hardening suggestions. There are also some hybrid environments with varying elements that you might need to be aware of.
Some Examples of Hardening
If you are wondering what you can do to harden your website, here are a few tips:
- Keep your CMS and extensions updated.
- Always install security patches to your CMS and extensions.
- Monitor your website and keep up with its log activity.
- Install a firewall on the device you use to access your website.
- Have long, unique, and complex passwords.
- Remove unnecessary plugins and extensions from your website.
- Use 2FA whenever possible.
- Install a Website Application Firewall.
Hardening a Website can be Difficult
The main issue with hardening is that not everyone is technical enough to follow or understand the guidance that this process entails. One of the challenges is to keep up with the newest vulnerabilities. Another challenge is time sensitivity.
5 Essential Checklist to Prevent CMS Websites from Hackers
Written by Sharifah Noor Sahila Syed Jamal(Source article was taken from: https://vinaora.com/5-essential-checklist-prevent-cms-websites-hackers/)
Creating a professional-looking website has become rather easy because of the availability of several Content Management Systems (CMS) across the web. Developing a website is, of course, a serious business and requires a thorough research about the trending web development technologies and resources. However, the selection of the CMS platform would be dependent on your web business’s purpose and the kind of website that you need in order to accomplish your organizational goals.
There are various CMS options available widely on the web. However, most of the websites are powered by the four major platforms- WordPress, Joomla, Magento, and Drupal.
Most of the people often think that their sites running on a specific CMS are safe and not really worth being hacked for. But, you must remember that websites are compromised all the times. Most of the security breaches do not aim to steal your data but because they want to use your server such as an email relay for spam or to set up a web server temporarily in order to serve files of an illegal nature.
As the owner of your website, there can be absolutely nothing more terrifying than seeing all of your work altered. Therefore, you should take some time out and protect your website. Listed below are a few measures that you can undertake in order to protect your CMS Based Websites from Hackers.
1. Avoid Using Default Admin as Your Password or Name
Hackers generally try to gain access to websites by guessing the default username and password. This means that if you are still using ‘admin’ as your username along with a password that is rather easy to guess for your admin login page, your website has higher chances of getting hacked. The hackers can make use of Brute force attacks and then enter an unlimited combination of the username of passwords till they find the one that’s correct.
No matter what CMS platform you are using, it is important that you always replace the default username with something that is more secure. Also, ensure that your password is unique, long and difficult to guess. Your password should, in fact, be a combination of alphabets, numbers and special characters. You can even use upper and lower-case letters. This would make it harder for the hacker to hack into your site.
2. Choosing a Great Hosting Platform
When it comes to strengthening the security of the Content Management Systems, selecting a good web hosting platform is rather important. With so many web hosting options available these days, it becomes pretty complex to choose the one that would be the best. Start-ups can use shared hosting as it provides the flexibility to enjoy unlimited resources at an economical price. However, it is best to choose a hosting platform which can offer impressive loading speed, robust security features, and other features.
Opt for a managed, VPS or a cloud server instead of shared hosting as these solutions have a far better security features and would also assist you in case your site ever gets hacked.
3. Keep the Platforms Updated
Ensuring that the platform and the scripts that you have installed are updated is probably one of the best things that you can do to protect your site from any security breaches. As most of the tools are developed as open-source programs, their codes are very easily available. This makes it easier for the hackers to pore over this code and look for security loopholes which would give them the chance to take control of your site by exploiting the platform.
For instance, if you have a site on WordPress, any of the third-party plugins which you have installed or the base WordPress installation are quite vulnerable to security breaches. Therefore, you should always make sure that you have the latest version of the platforms as well as the scripts installed. This would minimize the risk of getting attacked and takes very little time to do. The WordPress users can very easily get to know if there is an update available. Simply log onto your website and look for the update icon which would be on the top left corner very next to your site name. You would have to click on the number so as to access the WordPress updates.
4. Use a Two-Factor Authentication
Why use a two-factor authentication when you already have a secure username and password? Well, for the simple reason that having a secure username and password does not make your site completely safe from the malicious attacks. You can make use of a two-factor authentication in order to take the security of your website to another level. This would help in adding an extra layer of security. This means that at first you would have to enter your username and password and then would be required to enter a special security code which is created in every 30 seconds.
All you need to do is choose the extension or plugin that is relevant to your Content Management Systems platform and then tighten your admin login page’s security.
5. Using SSL/HTTPS Encrypted Connections
You can strengthen the security of your website by making use of SSL/HTTPS Encrypted Connections. A URL that is not encrypted would generally begin with https:// which actually makes your site prone to security attacks. However, connection to encryption regardless of whichever CMS Platform you are using can help you to prevent your site from the hackers. When you use encrypted connections, you can change the URL to https:// that adds an extra layer of security. The Secure Sockets Layer (SSL) would secure all of the information between the server and the client.
For instance, if you are using Magento CMS, the steps to encrypt your site has been shown below.
Login to the Admin Page > Click on Systems > Configuration > General > Web > Secure.
There, you would change the base URL setting from https:// to https:// and then click on ‘Yes’ in order to save the changes you just made. This would add an extra layer of security to your site and then you can utilize secure and safe fronted URL’s as well as Admin URL’s.
Summing up
Other than all of the above steps, it is important to make sure that your website is always backed up. The regular backup would ensure that your data remains safe. You can adapt all of the above-listed methods so as to make sure that your CMS website is safe from hackers.
Google reminds website owners to move to HTTPS before October deadline
Written by(Source article was taken from: https://blog.malwarebytes.com/101/2017/09/google-reminds-website-owners-to-move-to-https-before-october-deadline/)
With the release of Chrome v62 in less than 3 months, Google will begin marking non-HTTPS pages with text input fields—like contact forms and search bars—and all HTTP websites viewed in Incognito mode as “NOT SECURE” in the address bar. The company has started sending out warning emails to web owners in August as a follow-up to an announcement by Emily Schechter, Product Manager of Chrome Security Team, back in April.
Google began marking sites in Chrome v56, which was issued in January of this year. They targeted HTTP sites that collect user passwords and credit card details.
For owners to secure the information being shared among their visitors and their web server, they must start incorporating an SSL certificate. Failing to do this is risky for both parties: sites that allow the sending of information in clear text may also allow its exposure through the Internet.
Ms. Schechter also provided website owners with a handy guide on how to enable HTTPS on their servers. An additional guideline on how to avoid the “NOT SECURE” warning on Chrome is also available for web developers.
Looking at the way things are panning out, we can be confident that HTTPS will be the norm in no time. However, this doesn’t mean that all sites using SSL certificates can and should be trusted.
Google intended to separate phishing sites from legitimate ones with the marking of insecure sites, as Help Net Security noted in an article. Unfortunately, the introduction of new browser versions capable of flagging sites also promptly introduced more phishing sites using HTTPS. We’ve been seeing examples of this in the wild, as well, the latest of which was an Apple phishing campaign.
Discerning phishing pages from the real ones has become more challenging than ever. This is why it’s important for users to familiarize themselves with other signs that they might be on a phishing page apart from the lack of SSL certificates. Fortunately, users don’t have to look far from the address bar when they want to double-check that they’re on the right page before entering their credentials or banking details. Keep in mind the following when scrutinizing URLs and other elements around it:
- Look for letters in the URL that may have been made to look like another letter or number, or there may be additional letters or numbers in the URL. For example, examplewebsite.com may appear as examplevvebsite.com—Catch that? The double ‘v’ together makes it look like the letter ‘w.’ This is an example of typosquatting. Here’s another example: examp1ewebsite.com—the ‘l’ in “example” is actually the number one.
- Look for an Extended Validation Certificate (EV SSL). You know that a trusted website has this when you see a company name beside the URL, as you can see from the below UK Paypal address. Not all sites with SSL have this, unfortunately, but some of the trusted brands online already use EV SSL, such as Bank of America, eBay, Apple, and Microsoft.

Lastly, be aware that phishers may use a free SSL certificate in their campaign to make it appear legitimate. They may also hijack sites that already have SSL in place, adding more to the veil of legitimacy they want to attain.
More...
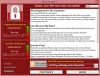
(Source ad image was taken from: https://en.wikipedia.org/wiki/WannaCry_ransomware_attack)
IMPORTANT TIP!
Have a backup solution of your important data (from time to time) in place such as keeping your important files in a 3rd party data storage (external hard disk, thumbdrive, DVD or CD) to evade ransomware attacks.
The WannaCry ransomware attack (or WannaCrypt, WanaCrypt0r 2.0,Wanna Decryptor) is an ongoing cyber-attack of the WannaCry ransomware computer worm targeting the Microsoft Windows operating system. The attack started on Friday, 12 May 2017, infecting more than 230,000 computers in 150 countries, with the software demanding ransom payments in the cryptocurrency Bitcoin in 28 languages. The attack has been described by Europol as unprecedented in scale.
The attack affected Telefónica and several other large companies in Spain, as well as parts of Britain's National Health Service (NHS), FedEx, Deutsche Bahn, and LATAM Airlines. Other targets in at least 99 countries were also reported to have been attacked around the same time.
Like previous ransomware, the attack spreads by phishing emails,but also uses the EternalBlue exploit and DoublePulsar backdoor developed by the U.S. National Security Agency (NSA) to spread through a network which has not installed recent security updates to directly infect any exposed systems. A "critical" patch had been issued by Microsoft on 14 March 2017 to remove the underlying vulnerability for supported systems,but many organizations had not yet applied it.
Those still running exposed older, unsupported operating systems were initially at particular risk, such as Windows XP and Windows Server 2003, but Microsoft has now taken the unusual step of releasing updates for these.
Shortly after the attack began, a web security researcher who blogs as "MalwareTech" accidentally found an effective kill switch, registering a website that was mentioned in the code of the ransomware. This slowed the spread of infection, but new versions have now been detected that lack the kill switch.
Background
The purported infection vector, EternalBlue, was released by the hacker group The Shadow Brokers on 14 April 2017, along with other tools apparently leaked from Equation Group, believed to be part of the United States National Security Agency.
EternalBlue exploits vulnerability MS17-010 in Microsoft's implementation of the Server Message Block (SMB) protocol. Microsoft had released a "Critical" advisory, along with an update patch to plug the vulnerability a month before, on 14 March 2017. This patch fixed several client versions of the Microsoft Windows operating system, including Windows Vista onwards (with the exception of Windows 8), as well as server and embedded versions such as Windows Server 2008 onwards and Windows Embedded POSReady 2009 respectively, but not the older Windows XP, according to Microsoft. According to Dona Sarkar, head of the Windows Insider Program at Microsoft, Windows 10 was not affected; however, IT writer Woody Leonhard questioned if this is the case with all Windows 10 systems, or just builds 14393.953 and later.
Starting from 21 April 2017, security researchers started reporting that computers with the DoublePulsar backdoor installed were in the tens of thousands. By 25 April, reports estimated the number of infected computers to be up to several hundred thousands, with numbers increasing exponentially every day. Apparently DoublePulsar was used alongside EternalBlue in the attack.
Attack
On 12 May 2017, WannaCry began affecting computers worldwide. The initial infection might have been either through a vulnerability in the network defenses or a very well-crafted spear phishing attack. When executed, the malware first checks the "kill switch" domain name.[a] If it is not found, then the ransomware encrypts the computer's data, then attempts to exploit the SMB vulnerability to spread out to random computers on the Internet, and "laterally" to computers on the same network. As with other modern ransomware, the payload displays a message informing the user that files have been encrypted, and demands a payment of around $300 in bitcoin within three days or $600 within seven days.
The Windows vulnerability is not a zero-day flaw, but one for which Microsoft had made available a security patch on 14 March 2017, nearly two months before the attack. The patch was to the Server Message Block (SMB) protocol used by Windows. Organizations that lacked this security patch were affected for this reason, although there is so far no evidence that any were specifically targeted by the ransomware developers. Initially, any organization still running the older Windows XP was at particularly high risk because no security patches had been released since April 2014 (with the exception of one emergency patch released in May 2014). However, after the outbreak, Microsoft released a security patch for Windows XP on 13 May 2017, the day after the attack launched.
According to Wired, affected systems will also have had the DoublePulsar backdoor installed; this will also need to be removed when systems are decrypted.
Ken Collins of Quartz wrote on May 12 that three or more hardcoded bitcoin addresses, or "wallets", are used to receive the payments of victims. As with all such wallets, their transactions and balances are publicly accessible even though the wallet owners remain unknown. To track the ransom payments in real time, a Twitterbot that watches each of the three wallets has been set up. As of 15 May 2017 at 7 PM, a total of 220 payments totaling $59,747.53 had been transferred.
Impact
The ransomware campaign was unprecedented in scale according to Europol. The attack affected many National Health Service hospitals in England and Scotland, and up to 70,000 devices – including computers, MRI scanners, blood-storage refrigerators and theatre equipment – may have been affected. On 12 May, some NHS services had to turn away non-critical emergencies, and some ambulances were diverted. In 2016, thousands of computers in 42 separate NHS trusts in England were reported to be still running Windows XP. NHS hospitals in Wales and Northern Ireland were unaffected by the attack.
Nissan Motor Manufacturing UK in Tyne and Wear, England halted production after the ransomware infected some of their systems. Renault also stopped production at several sites in an attempt to stop the spread of the ransomware. The attack's impact could have been much worse had an anonymous security expert, who was independently researching the malware, not discovered that a kill-switch had been built in by its creators.
Cybersecurity expert Ori Eisen said that the attack appears to be "low-level" stuff, given the ransom demands of $300 and states that the same thing could be done to crucial infrastructure, like nuclear power plants, dams or railway systems.
Microsoft has also released patches to fix the exploit used by the ransomware on the operating systems Windows XP, its 64-bit counterpoint, Windows Server 2003, and Windows 8, even though they all have been unsupported during that time.
**For more article info please visit the source: Wikipedia Website
Access, Sync and Share Your Data, Under Your Control!
credit: https://owncloud.org/features/
Access, Sync and Share Your Data, Under Your Control!
ownCloud is a self-hosted file sync and share server. It provides access to your data through a web interface, sync clients or WebDAV while providing a platform to view, sync and share across devices easily — all under your control. ownCloud’s open architecture is extensible via a simple but powerful API for applications and plugins and it works with any storage.
Access everything you care about
Store your private pictures, documents, calendar and contacts on your ownCloud server at home, a rented VPS or use one of the public ownCloud providers. Access your existing data on an FTP drive at work, images shared with you on Dropbox, or your NAS at home--all through your ownCloud server.Run your ownCloud server in a place you trust and access all the data you care about in one place!
Your data is where you are
When traveling, access ownCloud through your Android or iOS devices. Automatically upload pictures after taking them. Sync files at home or work with the desktop client keeping one or more local folders synchronized between devices. And wherever you are, the web interface lets you view, share and edit your files alone or with others.
Wherever you are, your data is with you thanks to ownCloud!
Share with anybody on your terms
Send password protected public links so others can upload files to you; get notified on your phone when you get a share from your own or another ownCloud server. Edit documents together, have video calls over your own server, comment on pictures shared with or by you. Don't be alone!
With ownCloud, you easily share and collaborate with whomever you want.